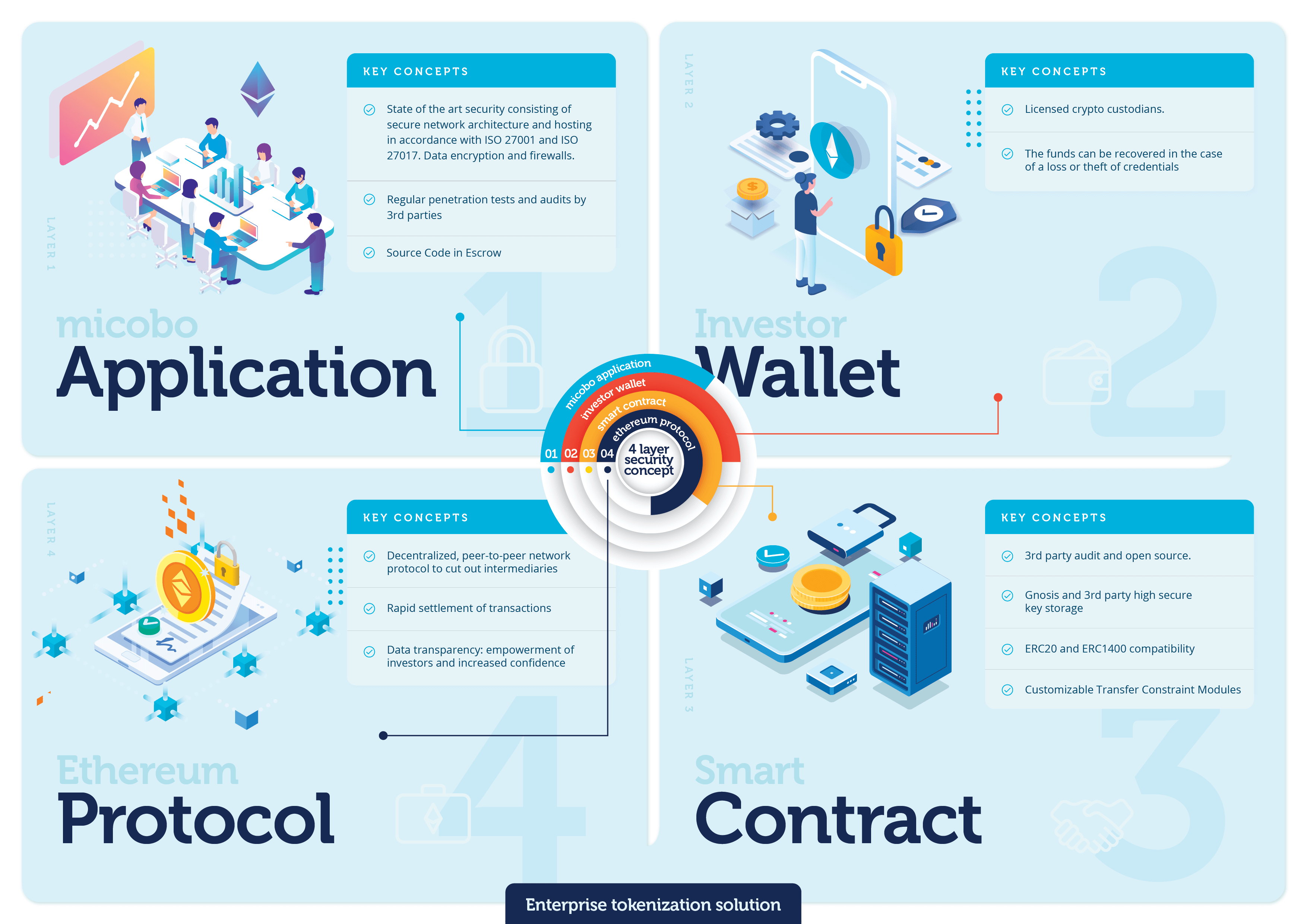
Bank-Grade Security
Compliant infrastructure to securely and efficiently tokenize assets
Compliant infrastructure to securely and efficiently tokenize assets


micobo Software Solutions & Services are compliantly available in Europe & Asia, and expanding to other jurisdictions, to drive asset tokenization operations at an optimal level.
Our services have passed extensive technical and regulatory considerations , to deliver stronger capability, financial compliance, protection of data, notice to data residency, and latency.
micobo services are built for resiliency including high availability and disaster recovery. There are no services that are dependent on a single logical data center (to avoid single points of failure). All Microsoft Azure services that store customer data are compliant with the European framework (Regulation EU 2016/679 General Data Protection Regulation - GDPR ) and national implementations allow the customer to specify the specific regions in which their data will be stored.
In accordance with our legal domicile and company registry in Germany, this documentation provides micobo’s technical and organizational resources on the basis of section 25a (1) of the German Banking Act (Kreditwesengesetz) – in particular for IT resource management and IT risk management, implementing the European Directive 2013/36. This is without prejudice to the requirements contained in the Minimum Requirements for Risk Management (Mindestanforderungen an das Risikomanagement – MaRisk).
The depth and scope of the topics addressed in this documentation are not exhaustive, and follow the legal requirements established by AT 5 and 6 of MaRisk. Hence, pursuant to section 25a (1) number 4 of the German Banking Act in conjunction with AT 7.2 number 2 of MaRisk, we observe and apply generally established standards to the arrangement of the IT systems and the related IT processes, as the IT Baseline Protection manuals (Grundschutz) issued by the Federal Office for Information Security (BSI) and standard ISO/IEC 2700X of the International Organization for Standardization.
Two Factor Authentication
Discretionary enabled with Auth0 under clients’ requests.
Advanced DevSecOps
Using Terraform for reproducible environments, with several security tools for code and container analysis.
Logging and Monitoring
Microsoft Azure and further developing to use advanced tools like Prometheus (Monitoring) and Loki (Logs).
Secure Data Encryption
Microsoft Azure encrypts KYC data at rest. All data in transit is encrypted with TLS 1.2, and DataBase is unencrypted.
Authentication & Access Control
Auth0 based and role-based access to functionalities, with robust API key management.
Data Backups
Through Microsoft Azure with regular storage and DataBase backups.
Service Resilience & Risk Avoidance
Microsoft Azure-based auto-healing of services and DoS protection. Additionally, we run manual load tests to gather performance data on the app behavior to check for improvement points.
Decentralized Issuing
Security Token deployment on the Ethereum Mainnet.
Auth0 for secure Oauth based login.
Microsoft Azure key vault for secret storage.
Infrastructure hosted in West Europe/Germany observing GDPR compliance.
According to AT. 2.3.3 of MaRisk, the initial issue of securities does not generally constitute trading. However, the first-time purchase of newly issued securities does constitute a trade within the meaning of the regulation, and hence we offer compliant management of the underlying software provided to perform these actions. In the case of first-time purchases, market conformity is verified following BTO 2.2.2 of MaRisk.
micobo advises its clients to subject their security token trades to ongoing controls. In particular, we offer support to comply with regulatory demands, providing verification on whether:
Being a DLT-based provider, we ensure security by storing complete transaction records on the blockchain. We use Microsoft Azure with regular storage and DataBase backups.
Our networks are segregated based on criticality levels, with development and testing environments hosted in an entirely separate Microsoft Azure project from our production environment. All networks are carefully segmented using tightly-defined firewall rules defined on a per-port and protocol level, both externally and internally
Security is the core of our operations, for which we are committed to ensuring the utmost account of every safety measure required by the regulators to provide compliant software. micobo stays ahead of the latest IT methods to provide transparent and protected services, guaranteeing security management to prevent risks and mitigate breaches.
We perform regular penetration tests by a recognized party, to make sure that our solution is built in full compliance with the latest requirements for IT-Security. We have made our audited smart contracts standard open-source for the community to check it and contribute.
We secure our clients by providing software escrow services that allow our clients to operate micobo’s enterprise solution under all circumstances (i.e., business continuity ensured).
micobo services are built for resiliency including high availability and disaster recovery. There are no services that are dependent on a single logical data center (to avoid single points of failure).
We ensure the mitigation of risks and recovery strategies through a compliant Business Continuity Plan (BCP) and a Recovery Strategy, as required by AT 7.3 (Contingency Plan) of MaRisk. Our clients receive a reference tool for the actions required during or immediately following an emergency or incident that threatens to disrupt normal business activities.
All Microsoft Azure services that store customer data are compliant with the European framework (Regulation EU 2016/679 General Data Protection Regulation - GDPR) and national implementations allow the customer to specify the specific regions in which their data will be stored.
micobo coordinates tasks, competencies, responsibilities, controls and reporting channels required for the management of information risk, in observance of AT 4.3.1 of MaRisk. To this end, we have in place appropriate monitoring and steering processes, paired with the related reporting activities, in observance to AT 7.2 number 4 and BT 3.2 number 1 of MaRisk. Therefore, our relevant business operations, services development and updates are adequately informed to our clients and licence holders.
micobo ensures the integrity, availability, authenticity and confidentiality of the data used by our IT systems and related IT processes, observing AT 7.2 number 2 of MaRisk. For these purposes, we use sophisticated management provided by Microsoft Azure Cloud Storage and Hosting Services.